Bitcoin dust attack myths and misconceptions
What is dust?
Bitcoin dust refers to UTXOs with tiny values that are so small that they are economically unspendable. That is, it costs more (in transaction fees) to spend than the value of the UTXOs. It’s possible to end up with dust in your wallet due to poor UTXO management. It’s also possible to receive dust deposits that you did not request. This is because you can’t stop someone from sending funds to a valid bitcoin address and every bitcoin address that has ever received funds is publicly viewable on the blockchain.
Cleaning up bitcoin dust in your wallet can be slightly detrimental to your funds and to your privacy. However, misconceptions around these issues have caused their severity to be overstated. In general, receiving a dust deposit is not something you need to be particularly concerned about in terms of bitcoin security.
A number of websites describe “dust attacks” as some sort of scary exploit that will cause you to lose funds. Here’s a snippet from Binance Academy:
A dusting attack refers to a relatively new kind of malicious activity where hackers and scammers try to break the privacy of Bitcoin and cryptocurrency users by sending tiny amounts of coins to their wallets. The transactional activity of these wallets is then tracked down by the attackers, who perform a combined analysis of different addresses to deanonymize the person or company behind each wallet. If successful, the attackers may use this knowledge against their targets, either through elaborate phishing attacks or cyber-extortion threats.
I have never heard of a single phishing or extortion attack against a bitcoin holder in which they became a target due to blockchain analysis via dust deposits. I consider statements like this to be FUD; while it’s technically possible it’s incredibly unlikely.
The real deal on dust
Why would someone want to send dust?
- To annoy bitcoin users
- To get their attention and advertise something to them
- To trick recipients into using more block space, jacking up the fee rates
- To trick recipients into correlating more of their wallet addresses
As a developer who has been building bitcoin wallets for many years, whenever users get a drive-by dusting it seems they always assume it's the last point. There is a strong narrative of "dust attacks" being an attack on privacy, but I've yet to come across any evidence that blockchain analytics companies employ these tactics. While we need not take analytics companies at their word, it’s worth noting that these companies have gone so far as to explicitly state that they do not engage in this behavior.
While it certainly is possible to be targeted by a blockchain analysis attacker, this would most likely only be performed by a law enforcement investigator who is trying to track funds tied to a crime. That’s because dusting a wallet is insufficient in and of itself; you can only gain further information about the identity of a wallet owner if you can then tie funds to an entity such as an exchange or payment process that you can subpoena to gain access to private information such as server logs or KYC data. Without such access, there is little to gain from dusting wallets. In such cases, the dust deposits would be of minimal volume and would not be targeting thousands of wallets simultaneously.
If you find yourself receiving dust, you can go check the transaction on a block explorer. It's likely that you will discover it's some form of spam or advertising. For example, we have recently seen spam transactions such as this one with vanity address outputs pointing to a URL on a BSV forum.
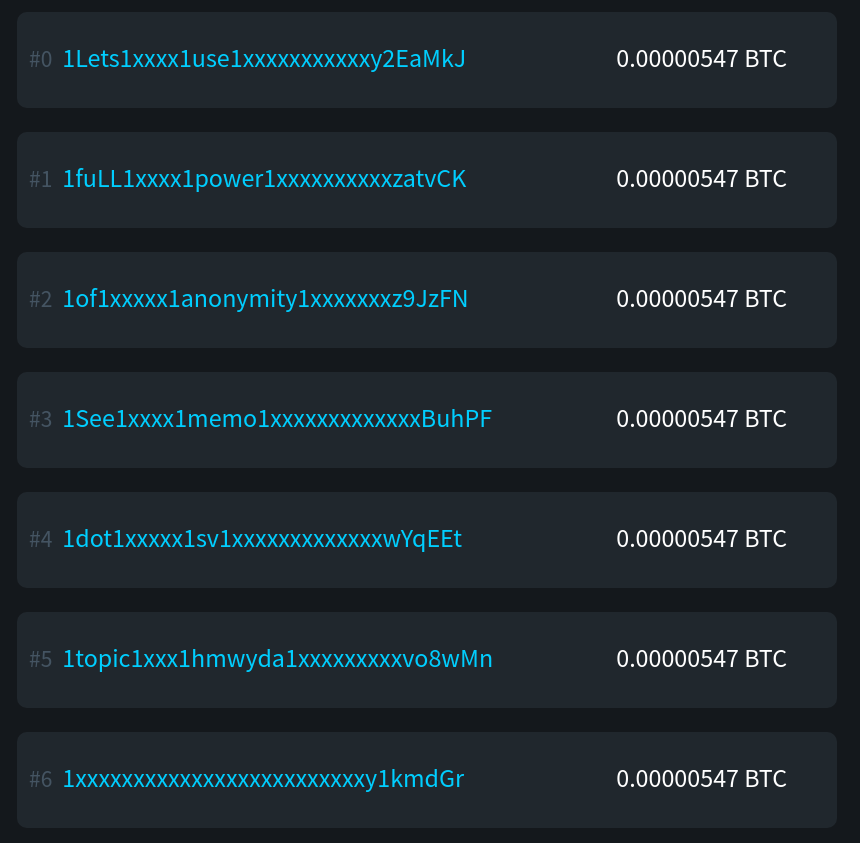
If you want to read a deep dive into the history of dust attacks, check out this analysis I performed recently. I was able to observe a number of trends, including the fact that the total volume of dust outputs being created has been on the decline since 2015.
By analyzing blockchain data for patterns and threading together other public information, we can see that the vast majority of dust outputs are clearly tied to spam and advertising campaigns. Different dust storms have been generated for different end goals, but it’s pretty clear that the goals were not for the primary purpose of stripping away people’s privacy.
Want to know more about privacy and security?
Our weekly Casa Security Briefing gives you quick and easy tips on digital privacy and ways to secure your crypto while breaking down the latest news. Sign up for free below.
