Security issues with browser-based bitcoin wallets
When we talk about security for bitcoin wallets the focus is often upon keeping the private keys out of the hands of the wrong people. It's generally understood that if an adversary gains access to your private keys, it's game over.
However, there is more to the security of a wallet than just controlling access to the private keys. We should also be concerned with how deposits and withdrawals are made to and from the wallet, as these are sensitive operations that can potentially be hijacked by an adversary in order to reroute funds to an address controlled by the attacker.
While no wallet software can protect you against every security issue, at Casa we have concluded that browser-based wallets are the most vulnerable for a variety of reasons.
Phishing
Phishing is the practice of tricking a user into using malicious software that is designed to look legitimate. The malicious site may try to harvest credentials or trick a user into downloading a tampered version of a wallet.
For example, if you are tricked into logging into a malicious website at c0inbase.com, the attacker can collect your username, password, and even 2FA to access your Coinbase account. We've seen scammers manipulate ads on search engines for years in order to trick users into providing their login credentials.
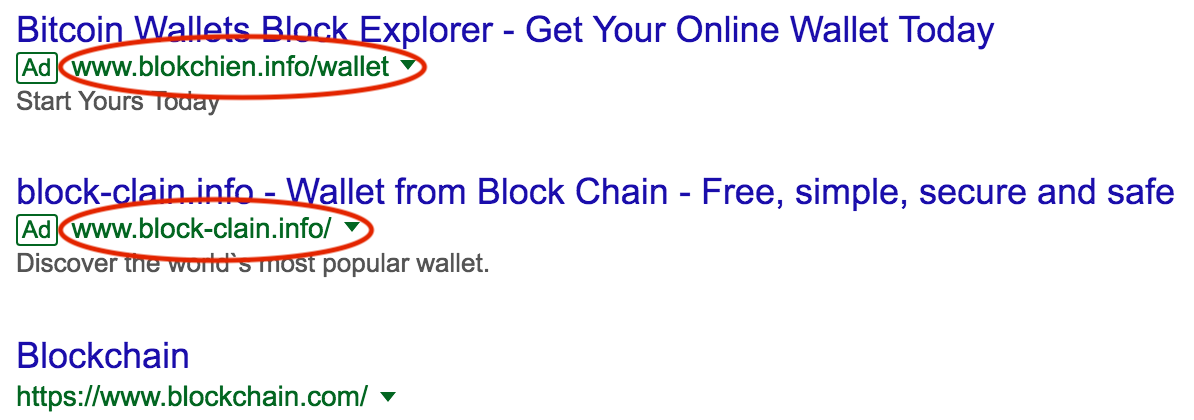
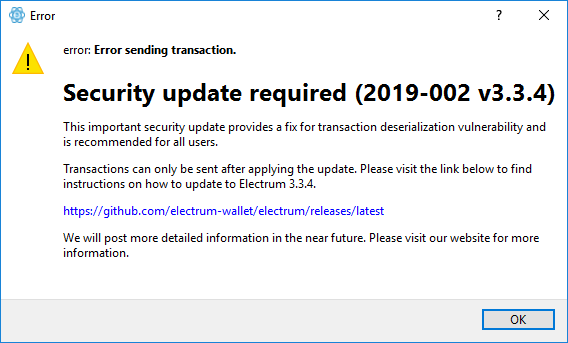
While phishing attacks against web wallets is a common practice, it has even occurred against desktop wallets that connect to remote servers. Users of Electrum wallets were phished with a false upgrade notice, tricking them into downloading a version of the software that steals their private keys.
Even Trezor users, whose private keys are kept secure on dedicated hardware, found themselves targeted at a weak point: the web-based Trezor wallet. Only particularly astute victims who noticed that the SSL certificate didn't match the domain would be aware that this was not the real Trezor wallet software.
We have also seen impostor Trezor sites pop up; users who accidentally mistype the "trezor.io" URL may be redirected to a malicious site that looks and feels exactly like Trezor's web wallet, but will instead try to trick the user into entering their seed phrase.
Attackers are well aware that they can't remotely siphon the private keys off of dedicated hardware devices, thus they're exploiting weaknesses in the software that is being used to interface with the device. To date these attacks are fairly unsophisticated and ask the user to type in their seed phrase, which should raise a huge red flag, yet plenty of users still get tricked. We expect the sophistication of these attacks shall continue to increase.
Malware
Wallet software that runs on desktop operating systems are also vulnerable to malware that can compromise deposit & withdrawal operations. This is because desktop operating systems tend to have large attack surfaces and are used for a wide variety of operations that can be exploited as vectors for installing malware. Clipboard malware, for example, has been found in the wild for several years now.
In June of 2019, Coinbase employees were targeted with a 0-day exploit against the Mozilla Firefox browser that enabled an attacker to completely take control of the victim's machine.
We've even seen bad actors gain control of popular JavaScript libraries that are known to be used by bitcoin wallet software, in order to inject malware that steals private keys. This is a particularly challenging problem for many browser based wallets since many are built with JavaScript.
It was recently discovered that hackers have been distributing compromised versions of Tor Browser for years; the browser itself had bitcoin address swapping built into it.

There's a reason why the gold standard for bitcoin wallet security is to use a dedicated hardware device such as a Ledger/Trezor/Coldcard/etc.
The device both protects your private keys from attackers and runs software that is highly resistant to tampering, ensuring the integrity of generated receive addresses displayed on the device's screen.
Any software that runs on a general purpose computing machine is going to be more easily attackable, though mobile phone operating systems do tend to be more robust against tampering and are better at locking down running applications via sandboxing.
Who is vulnerable to these issues?
While desktop or mobile wallets could be exploited under the right conditions, any web-based wallets, web-based exchanges, and even web-based payment processors are operating with a particularly weak security posture against these threats.
And there's not a whole lot that can be done by these service providers because the security issues are not confined to weaknesses within their own infrastructure that they control, but are in many cases are end-point issues that are reliant upon users following good security practices.
To protect against malware, a browser-based wallet should only be used on a dedicated single-purpose air-gapped computer. Due to the complexity of setting up an air-gapped system, most users will neglect to do so, putting their funds at risk.
Browser extension risks
One particularly disturbing issue with web browsers is that browser extensions can easily get full control of all data that is accessed and rendered by the browser. In late 2018 Kaspersky came across a trojan that specifically targeted web browsers and installed malicious extensions.
"The function findAndReplaceWalletAddresses searches for Bitcoin and Ethereum wallets and replaces them with the addresses of the threat actor’s wallets. Notably, this function works on almost all pages except those located on Google and Yandex domains, as well as on popular domains like instagram.com and ok.ru. Images of QR codes that point to wallets also get substituted."
To gain a better understanding of the capabilities of browser extensions to attack browser based wallets, we tasked an engineer who had built the Casa browser extension to build a proof of concept extension that posed as something innocuous while actually being malicious. It took this engineer less than a day to come up with an extension that posed as a wallpaper library but was capable of replacing deposit addresses and scraping a variety of sensitive data that would be sent to a remote server for analysis.
In the following clip former Casa CEO Jeremy Welch demonstrates the malicious browser extension capturing bitcoin addresses and sending the data to a third-party server.
In this clip Jeremy demonstrates the malicious browser extension modifying a receive address displayed in a wallet's web interface.
Casa security
We suspect that browser security issues are one of the reasons that Ledger discontinued support for its Chrome applications and instead direct users to install their desktop application, Ledger Live. So how does Casa's solution stack up against these threats?
We've basically solved the problem of accidentally withdrawing from the wallet to an attacker's address. A user has to confirm their withdrawal address on (possibly multiple) hardware devices, thus requiring a high level of negligence on the part of the user in order to send to an unintended address.
The problem of an attacker swapping out the deposit address is not fully solved, but we have made it very difficult.
Address spoofing
While Casa's Key Shield is highly secure due to the geographically distributed nature of the private keys, the user still needs to obtain a deposit or destination address for each transaction to & from wallets outside Casa’s systems. Malware on a user’s computer can cause their web browser or other wallet software to display an incorrect address. This would defeat the security of any storage system, as it occurs outside of that system.
How we mitigate this issue:
- Use of a mobile app mitigates browser based address modification. While it doesn't make all malware impossible, it raises the difficulty significantly due to a variety of controls that ensure the integrity of the software. All mobile app builds must be cryptographically signed with a key only held by a Casa security officer, mitigating external attackers from deploying a malware-laden version of the app. Our build process uses two-man rules to ensure that builds cannot be signed off by the app developers, thus mitigating internal attacks by a compromised employee.
- Casa re-derives addresses independently on both our server and mobile devices. The integrity of address derivation on the server is additionally ensured via HMACs on the extended public keys that are added by our hardware security module. The mobile app will throw an error if there is a mismatch between server and mobile device.
- Use of Casa’s Sovereign Recovery data allows for additional validation of addresses via independent open source software. This is still an area of ongoing research to implement more user friendly methods for this external check.
Future improvements
Partially Signed Bitcoin Transactions (BIP 174) enable hardware devices to check the integrity of change addresses by passing extended public keys and derivation paths along with the change address, ensuring that they actually belong to the wallet.
Open sourcing software generally provides more trustworthiness but there are complications when it comes to mobile apps. We are not currently aware of a way to prove that the software installed via the iOS App Store or Google Play Store is the same software that is available in an open source repository.
A payment protocol that involves the receive address being cryptographically attested to by the recipient could also improve the integrity of payments by eliminating man in the middle attacks. BIP 75 does this; it was proposed back in 2016 but never got much adoption due to privacy and fungibility concerns. As of today, it's recommended that when sending a high value bitcoin transaction you confirm the receive address out of band (via video/audio) to ensure it is correct.
Don't trust your browser; verify sensitive operations with other hardware and software!
Looking for more security knowledge?
Our weekly Security Briefing newsletter provides quick updates on bitcoin security with analysis from Casa’s experts. Sign up here.

