The evolution of bitcoin key management
Let’s revisit important milestones in how we experienced Bitcoin HODLing over the past 10 years, and what we can expect from 2019.
In this post, I’m not talking about custodial “vaults” — exchanges and wallets that hold crypto on the customer’s behalf — nor all the security faux-pas and breaches that happened in custody. This is merely my appreciation for the development of the sovereign Bitcoiner.
In the early days of Bitcoin, private keys were stored as plaintext in a wallet.dat file on your computer drive. There was no password to protect this file, no means of importing or exporting your private keys, and keys were generated via command-line python scripts. *shudders* Spooky stuff. The security risks of such a setup were innumerable, and it wasn’t until core developers took to Bitcoin Improvement Proposals (BIP) that security really began to strengthen.
Nondeterministic wallets
Nondeterministic wallets are those where each key is independently generated from a random number. The first bitcoin wallet apps were nondeterministic desktop wallets, which generated a random set of bitcoin addresses and corresponding private keys (key pairs). Users had to back up their key pairs after each transaction to be 100% sure not to lose funds. However, users often ran into different issues, such as a limited number of unique addresses, failure to back up the most recent change in addresses, or losing money due to bad UX (accidentally entering a transaction amount into the fee field). The first desktop wallets were an important step towards a non-developer audience, and allowed the earliest adopters to use Bitcoin without too much command-line voodoo.
Despite rising privacy concerns about reusing the same address to receive multiple payments, it took some time for Bitcoiners to switch to wallets that automatically generated fresh addresses for each transaction. That said, there are still situations where a single key wallet comes in handy.
A single key wallet can be used to create a paper wallet, which you can carry among your credit cards and use to pay for a coffee or receive money from a friend while you’re offline.
Peter Kroll’s Bitaddress.org was the first to introduce a user-friendly and popular paper wallet generator.

However, generating wallets online is considered insecure. It only takes a keylogger on your computer to put all the deposited Bitcoin at risk. Generating keys offline was possible, but that required a certain level of command-lining too.
For a while, there wasn’t both a secure and user friendly solution for paper wallets. The first hardware to solve for this was Piper, a printer made from a RaspberryPi, which made paper wallets on demand.

We love to feel money. We are used to printed paper, metal coins and a rectangular piece of plastic that represents the digital money in our bank accounts. That same desire for physical touch was embodied in the first physical bitcoins, called Casascius coins — metal coins created by Mike Caldwell in 2011. Casascius coins hid the private keys safely under a holographic seal and came pre-loaded with bitcoins in several denominations. This continued until FINCEN began requiring a license for their production.

In April of 2013, BIP-38 introduced password encryption for physical wallets — more specifically, for physical bitcoins and paper wallets. BIP-38 advanced the security of these cold storage solutions, but they still aren’t recommended for holding substantial amounts of crypto due to their many potential security pitfalls.
Thanks to NFC and RFID technology, physical bitcoin has taken on a range of forms, from a plastic card or teddy bear to a bitcoin wallet implant in the palm of your hand.
Deterministic wallets
Today, bitcoin wallets generate addresses in a deterministic way. They take an initial input (called a “seed” by cryptographers) and derive a multitude of addresses from it.
Late 2011 saw the birth of Electrum, the first deterministic wallet. Users could finally recover all their bitcoin holdings using one seed, and were freed from painfully frequent back-ups.
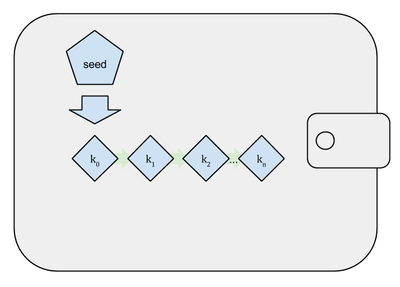
The first deterministic wallets were relatively basic. One master key could make multiple addresses (Image A), but wallets weren’t capable of anything more complicated than one level of derivation — one master key with many child keys.
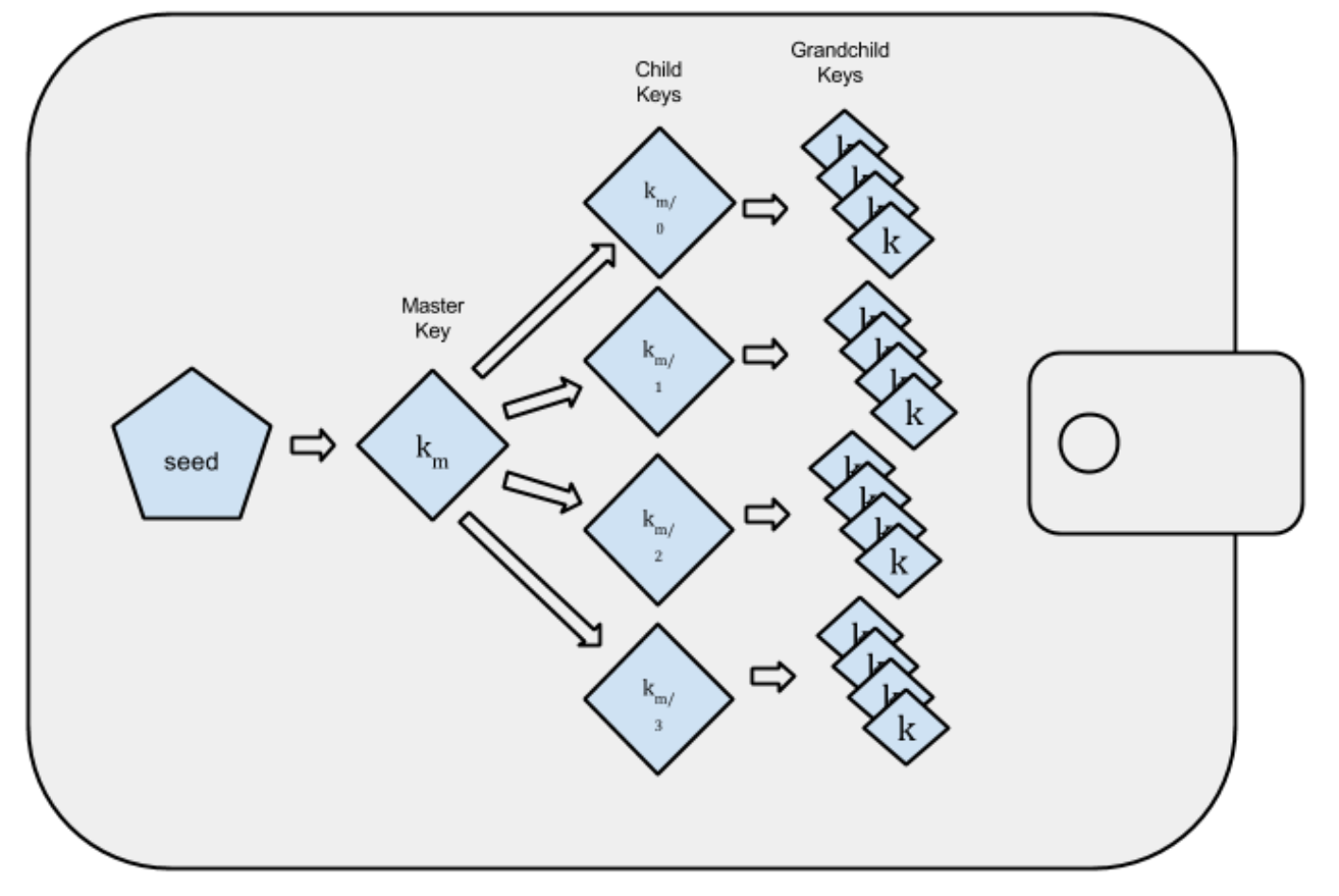
Then, in 2012, BIP-32 brought us the HD wallet. Contrary to your first instinct, it has nothing to do with “high definition.” HD wallets added a hierarchical structure to the deterministic wallet (Image B), hence their name: Hierarchical Deterministic wallets.
HD wallets offered an important practical benefit: wallet structure could now express a greater degree of organization. Imagine setting up one single wallet for multiple coins, each with an (almost) unlimited number of sub-accounts for different purposes (saving, business, shopping) and each account with an (almost) unlimited number of unique addresses — all derived from and backed by one single seed.
The mnemonic seed
Although mnemonic seeds had already been used by Electrum, BIP-39’s arrival set the standard for modern mnemonics. BIP-39 defined a list of 2048 english words making bitcoin wallets easily portable or recoverable across different wallet software, provided they follow the same BIP-39 standard.
Any modern bitcoin or cryptocurrency wallet will give you a sequence of 12 to 24 mnemonic seed words during the initial setup, also called a recovery seed or recovery phrase, and will ask you to write these words down on a piece of paper. This ensures that your phrase can never be stolen by a computer virus.

To protect the recovery seed against theft by an “evil maid,” a passphrase encryption of the seed was added, also known as the 25th word, or a seed extension. It works similarly to two-factor authentication.
Despite the convenience of backing up crypto wealth easily and protecting that back-up against theft, the need to securely store the recovery seed paper inadvertently created a new potential for security failure.
In an effort to fortify the security of private keys, custodial solutions began implementing split wallets in early 2014. Split wallets utilized a method of cryptography called Shamir’s Secret Sharing. This meant splitting a private key into multiple parts, known as shares, so that securing a private key meant identifying and combining a predetermined minimum threshold of shares.
The hardware wallet
After several hobby projects, ideas, and implementations (Armory) for secure offline “cold” storage, in 2012, my co-founders at SatoshiLabs prototyped the first commercial hardware wallet — Trezor.
Trezor implemented several important features which are still widely used today:
- HD wallet structure to support multiple coins and accounts
- A seed for easy recovery when lost or broken
- Additional passphrase encryption for plausible deniability
- A trusted display for verification of transaction details
- Buttons for physical confirmation of important transactions. This prevents malware from confirming actions, as is common with a software button.
- Most importantly, Trezor separated private keys from the Internet and onto a small electronic device.
Key management today
Bitcoin works best for you when nobody else is capable of moving or freezing your funds without your approval.
Casa is hard at work to ensure that you remain in command and we strive to offer the flagship key management solution for personal sovereignty and safety. We’ve come a long way since single key solutions, and we intend to set the bar high for industry-wide security standards.
